What's 🔥 in Enterprise IT/VC #338
🔥 up for RSA Security in SF
I’ll be heading out later today for RSA Security in SF and 🔥 up to see what’s in store from customer, vendors, and investors for the rest of 2023. As far as what I’m looking at heading into the conference, let’s start with the most recent Goldman Sachs IT Spending Survey from April 16, 2023.
You guessed it - “Security tops spending priorities again”
Security remains the top spending priority; other top priorities include SaaS Applications, BI/Analytics, Public Cloud, and Cloud-based Financial Applications. SaaS applications moved up to #2 from #3 and business intelligence/analytics moved down from #2 to #3. Public cloud spending moved up to the third spot from fourth and cloud-based financial applications moved up several ranks from #8 to #5. Public cloud infrastructure saw record adoption relative to prior surveys: Our CIO survey suggest that ~31% of workloads are now on the public cloud (vs 24% in June 2022) with ~51% of workloads expected to be on the public cloud in 3 years (~42% in June 2022). This surpassed the previous all-time high of 43% in December 2019. Azure continues to lead cloud workflow adoption as well as the top position in PaaS adoption expectations.
And within security, the cloud is on 🔥.
Here’s another look at how the mix has changed but but the Cloud has jumped from #4 to number 1 in just a few quarters.
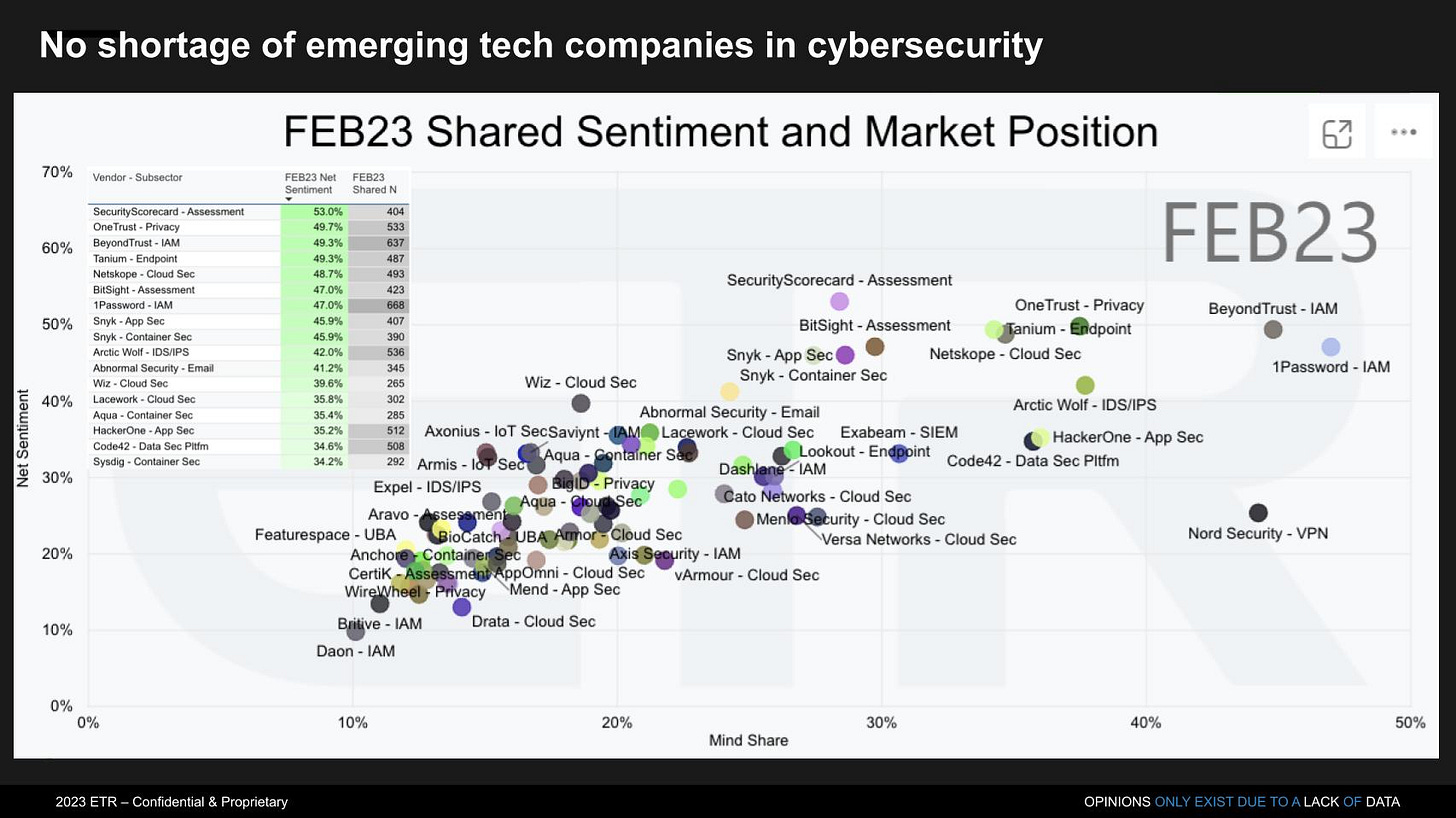
When it comes to Emerging Security Vendors, it’s great to see portfolio cos Snyk and Security Scorecard prominent here. More thoughts here on what to expect at RSA 2023 from Silicon Angle with data to support.
As for me, I’m 🔥 up to to dive into all things AI and security. This is one of biggest tailwinds we've seen in history and while many large enterprises are excited to leverage LLMs/GPT, they are also incredibly scared. Enterprises need to understand who is accessing data, create policies for how, manage authorizations, create basic classification to block, and in some cases leverage secure computing. We have a number of @Boldstartvc portfolio cos solving some of these problems including @capeprivacy, @ProtectAICorp, @bigidsecure, and @recolabs_ai.
Here’s an example of how to use LLMs like GPT4 on confidential data from Cape Privacy, a portfolio co.
Other ideas I keep thinking about is that while GPT and other models will scan code for vulnerabilities impacting revenue at some startups, on flip side, there will be more code than ever before and if these foundational models are trained on crappy code, this could be a massive shot in the arm for many SAST cos. In addition, now anyone who can write a prompt can sling code which means business users will have to have their code scanned as well - what tools will be available to protect that code from creating new security risks at enterprises. AI will also augment the security analyst helping find that needle in a haystack faster.
As always, 🙏🏼 for reading and please share with you friends and colleagues.
Scaling Startups
Risk/Reward - earlier you go the more equity you get in data from 2022 Carta
OpenView 2023 State of SaaS Talent Market for download here
8 in 10 candidates are scrutinizing company stability before accepting a role.
89% of C-Suite talent rate financial performance as a top criteria when evaluating an offer.
Navigating those pesky CFOs even after your champion says we are ready to go - great advice from Fabio
Enterprise Tech
🤯 the amount of compute!
What’s after GPT-4? Hyena? (ZDNet)
In a paper published in March, artificial intelligence (AI) scientists at Stanford University and Canada's MILA institute for AI proposed a technology that could be far more efficient than GPT-4 -- or anything like it -- at gobbling vast amounts of data and transforming it into an answer.
Known as Hyena, the technology is able to achieve equivalent accuracy on benchmark tests, such as question answering, while using a fraction of the computing power. In some instances, the Hyena code is able to handle amounts of text that make GPT-style technology simply run out of memory and fail.
get those SBOMs ready - a rare supply chain attack orchestrated by North Koreans
The massive 3CX supply chain attack, in which hackers hid malware in the VoIP firm's application, began when 3CX was breached with malware hidden in a legit trading app—perhaps the first confirmed case of one software supply chain attack causing another. (Andy Greenberg)
On what the new normal could be for Net $ Retention
with more from my Feb 18 post on what best in class NDR will look like this year
Google Bard now codes - code generation, debugging and explanation (Google Blog)
Stack Overflow Will Charge AI Giants for Training Data (Wired) - joins Reddit in charging for access to data to train algos
Get started with AutoGPT in seconds…